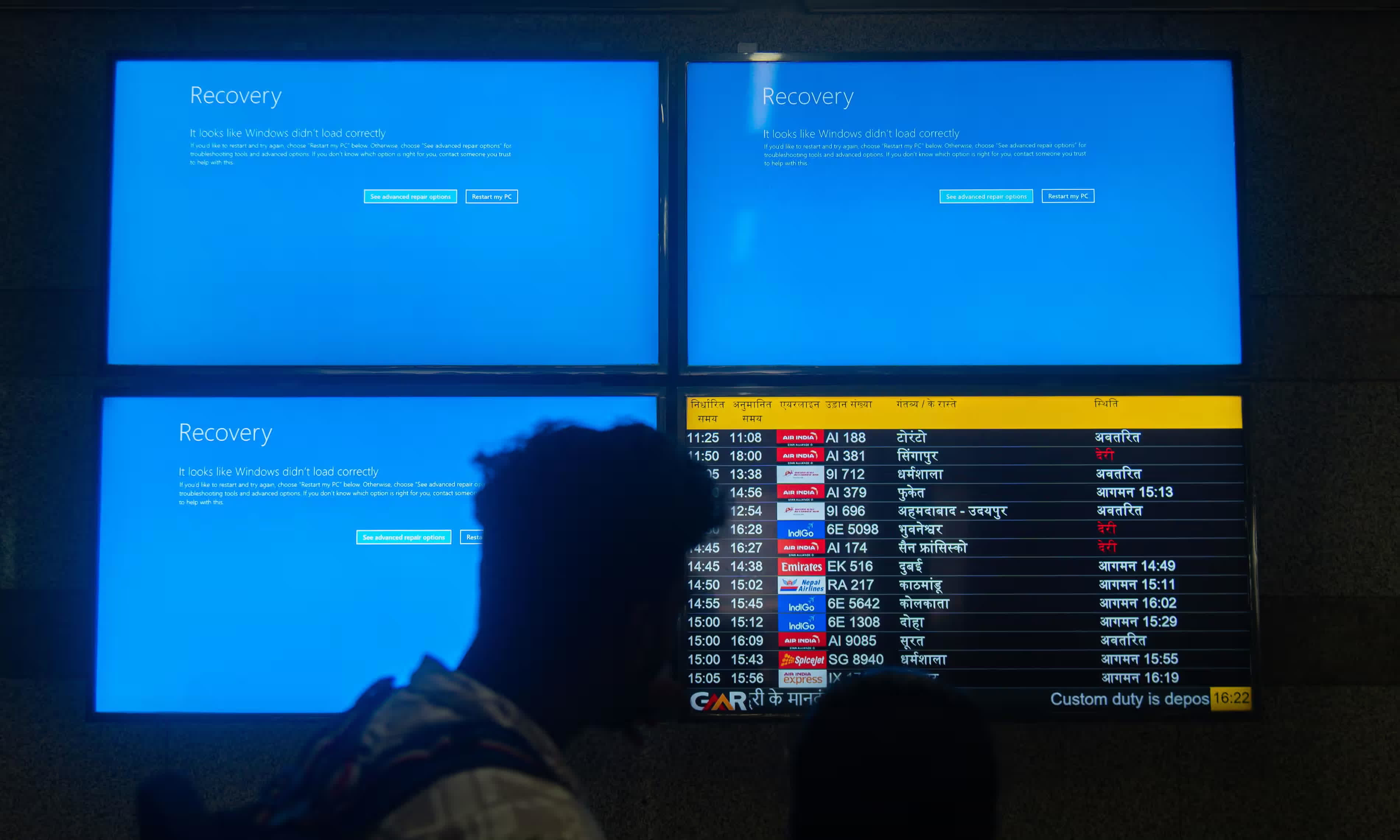
A hot potato: While still working with CrowdStrike to bring millions of botched PCs back online, Microsoft is also thinking about the future of Windows. The platform must evolve and innovate, enhancing resilience against the next faulty update coming from a third-party company.
The Crowdstrike incident could become a turning point for security across the entire Windows world. Microsoft received a big part of the blame and bad press for a bugged update released by Austin-based security company, and so, the Windows maker has started talking about improving resilience for its operating system. Even if regulatory agreements are saying otherwise, Redmond appears willing to make accessing the Windows kernel significantly more challenging than it is today.
“The Windows ecosystem is a broad, widespread, and open computing platform,” Microsoft VP John Cable said in a recent blog post. However, the CrowdStrike fiasco underscores the critical need for reliability within every organization. “Windows must prioritize change and innovation in the area of end-to-end resilience,” Cable stated, emphasizing that these changes are necessary to enhance OS security.
The main reason behind the Crowdstrike incident was a faulty update for Falcon Sensor, a vulnerability scanner working at the kernel level to detect and block threats. If a kernel driver crashes due to its own bugs, the entire Windows OS can be brought down despite Microsoft’s best efforts to avoid it. Microsoft has criticized European regulators for mandating open kernel access to external security vendors but remains committed to collaborating with partners “who also care deeply about the security of the Windows ecosystem.”
Security innovations mentioned by Microsoft include the recently introduced VBS enclave feature, which utilizes Hyper-V and Windows virtualization to isolate individual applications or specific routines in a protected memory region. Additionally, the Microsoft Azure Attestation (MAA) service can help verify the trustworthiness of a platform and the integrity of its binaries files.
Microsoft is carefully choosing its words, but it’s clear the company is interested in making Windows more similar to macOS regarding limiting kernel access by external security software.
The “zero trust” approach employed by VBS enclaves and MAA does not depend on kernel access to enhance Windows security, and Microsoft will will keep developing this kind of capabilities despite third-party antivirus programs still mingling with its OS’ innermost core.
CrowdStrike’s website earlier this week vs. now. Look at what magically disappeared: “Microsoft’s security products can’t even protect Microsoft. How can they protect you?” ðÂ¥² pic.twitter.com/B98P5m3kjf
– Tom Warren (@tomwarren) July 26, 2024
Microsoft also provided additional guidance on best practices organizations can adopt to improve resilience and avoid another CrowdStrike PC apocalypse. Companies need to implement proper business continuity plans and incident response plans, back up data “securely and often,” and ensure they can restore their Windows devices in a short timeframe.
Additional measures such as deployment rings, the latest Windows security default features, and a cloud-native approach to device management should be pursued as well.
